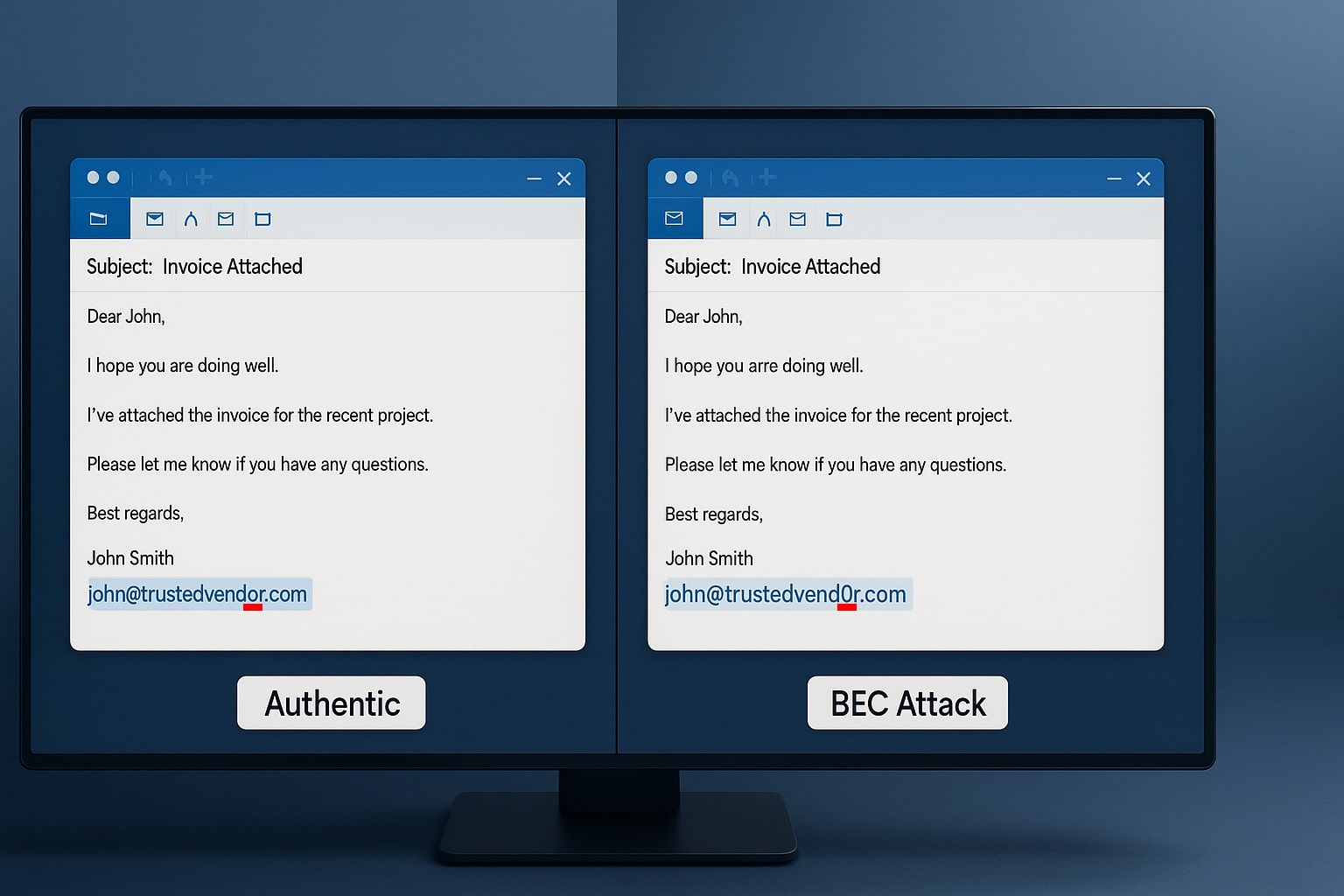
Risk assessments(1) are a necessary part of any business’ cybersecurity(2) strategy. You may be asking yourself, “what is the purpose of a risk assessment?”
The purpose of a risk assessment is to “bring to the surface things you can’t see,” notes Amir Sachs, CEO of Blue Light IT and bestselling cyber security author. “You are not aware of what you don’t see…if you come home after you’ve been out all day, and the house is all a mess and the drawers are on the floor, and everything is in a big mess…the first thing that goes through your head is…’I’ve been burglarized’. But you can see it with your eyes that something is wrong.”
“When it comes to your computer, you don’t know what valuables you have, you don’t know where they’re stored, because you just don’t see it. If you’re working at a company with 10 employees, the owner of the company puts in strict regulations that say no one can save files on their local computer, everything must be on the file server. But how does he really know this happens? He doesn’t.”
“You can go to each person’s computer and check it, but if he does this [throughout the week], when does he have time to do his actual job?”
“A cybersecurity risk assessment brings to the surface [or] it floats all the risks that a company has with regards to securing their data. It tells us things like this person is using a very old version of a software that is full of vulnerabilities, this person hasn’t updated his computer in six months, this person is [working] without an antivirus, we’ve found a document with all of your company passwords in a plain text file…this process brings all the [issues] to the surface so that the owner/manager is aware of the risks they have.”
“Once they have the results of the [risk assessment], they can act on those risks.”
The next logical step in questions you may have may be, “what is included in a risk assessment?” We’ve interviewed Amir Sachs to help explain in more detail what you can do as an individual to adequately prepare a risk assessment and ultimately implement a strong cybersecurity program.
Need to Find the Right Solution for You?
What Does A Risk Assessment Provide?
An in-depth Cyber Risk Security Assessment can provide:
- A list of vulnerabilities & risks that exist within your business IT
- The potential damage that these risks could create if left unresolved
- Steps to take to resolve these vulnerabilities and strengthen security
- Opportunities to streamline and improve existing IT systems
- Better compliance with laws and regulations
- A continuity plan to ensure your business can stay up and running
The most important benefit, however, is peace of mind—knowing your business is protected against threats from outside sources that may result in loss of sensitive data or financial damages.
How Safe is Your Data Storage?
To formulate and execute an effective information security program, you need to know what information you have and how/where it is stored. The risk assessment examines internal and external security factors as well as the confidentiality and integrity of your customers’ information.
Amir Sachs goes into more detail about risk assessments below.
What Does The Risk Assessment Process Look Like?
“A risk assessment has two portions to it, an interview section and a technical analysis. We discover the current security position of the company, we establish a baseline of where they are at the moment and identify high-risk security flaws, which offer easy access to hackers.
“The questions we ask help us to understand the risk to the business operation, and we estimate the financial impact of a security breach. The CSRA (cyber security risk assessment) is designed to investigate the existing business practices, test staff readiness and analyze business technology infrastructure to determine whether the people, processes and technology are aligned to repel cyber attacks and aligned internally with what they need to do.
“The results will give management of the company the facts regarding their business so ownership can make an informed decision regarding [the] next steps.
“The risk assessment is designed to accomplish three goals:
- Determine the state of the existing cyber security and information security processes, and any best practices within the organization.
- Identify any existing security gaps.
- Provide the executive team with a current picture of the organization’s ability and readiness to withstand a cyber attack.”
Need to Find the Right Solution for You?
What Do I Get at the End of the Risk Assessment?
“The report at the end of the assessment will highlight any gaps in their security and provide steps to remediate. They could take those steps and provide them to any IT company that does cyber security and the IT company will be able to implement and close the gaps. The technical analysis is done remotely.”
Leading You Back to Safety
Your company is like an island of safety – until you connect to the internet. Then it’s as if you’re doing business in a sketchy, crime-ridden neighborhood. Obviously, you have to be connected, so we take a hard look at where your company is at risk, then set about bridging gaps and reinforcing your boundaries. Awareness is the first step to improving security standards throughout your business. Let us give you a clear vision and a robust strategy to follow.
- Guaranteed recovery from cyber attacks
- Thousands of cyber threats tracked daily
- Safe, comprehensive data storage
If you’d like to learn more about risk assessments or if you have any questions related to cyber security, contact us(3) or book a meeting(4).
- https://www.bluelightit.com/cybersecurity-risk-assessment/
- https://www.bluelightit.com/cyber-security/
- https://www.bluelightit.com/contact/
- https://www.bluelightit.com/book-a-meeting/
Related Posts

Law Firms Beware: The Silent Ransom Group is Calling
read more
Slopsquatting: The AI Security Threat Every Development Team Must Address
read more